Online harassment can be alarming and stressful. In addition to the support resources discussed above, you may want to consider taking any of the following actions below to respond to an incident of online harassment. While this is not an exhaustive list of actions that can be taken, this guidance is meant to help you navigate situations of online harassment.
1. Revisit your Privacy Settings on Social Media Platforms
Most social media platforms have privacy or security settings that limit the ability of third parties to interact with your profiles or pages.
Consider reviewing and changing key settings on social media platforms in order to limit those who can see your information or engage with you. For instance:
- Who can see your profile?
- Who can add you to their profile or page?
- What personal information (email, location, workplace, other social media profiles, etc.) is visible to others?
- Who can send messages to you?
- Who can see or comment on your posts?
- Who can tag you in photos or posts?
Privacy policies and security settings change frequently and are different for each platform. For the most up to date information on privacy policies and security settings, you should visit the specific social media site to learn more about these settings.
2. Consider temporarily disabling your profile or, alternatively, making it completely private so that only your close connections can post or comment in your feed.
3. Ignore, if possible, comments and do not engage in “back and forth” comments
The goal of social media “trolls” is to elicit a response. Although you may wish to respond and defend yourself online, responding to the harassing messages of these “trolls” can tend to prolong and inflame incidents. While online attacks can certainly be intense, “trolls” tend to move on if you ignore them long enough.
4. Determine if “muting” the individual is possible and appropriate.
If comments are causing you distress, you have the option on some social media platforms to change settings to “mute” the user and their comments. The user normally is not notified that you have muted them, and you can ignore their comments. Bear in mind that by “muting” the user, you are not blocking them, and they may still be able to see your profile, so if you are worried their comments may become threatening or are directed to you, you may instead wish to consider “blocking” the user or “reporting” them to the social media platform (see below).
5. Block the User
Some social media platforms may allow you to block and prevent others from contacting you, following you, seeing your posts, or commenting on your content. You should be aware that, on some platforms, if you block someone, the individual may receive some form of notification.
6. Report the User
It is not recommended that you engage directly with the user account or website that is targeting you with abuse, harassment, or threats. If you see content on a social media platform or website that is directed at you and violates the site’s community standards, you should report the content to the platform or web host.
Depending on the platform and its terms of use, this could result in their account being suspended or the user being removed from the platform. Bear in mind, some posts might be harassing in nature but do not violate specific platform guidelines. Also, the user may have multiple or fake accounts; or the messages might come from multiple accounts and users.
Be advised: If you decide to submit a request to take down harmful content, you should first always save a copy of the content in order to preserve evidence of online harassment.
We have listed below the reporting links for some more popular social media sites:
- Blogger/ Blogspot: Content Policy; Report a Community Violation
- Facebook: Community Standards; Report Something
- Instagram/ Threads: Community Guidelines; How to Report Things.
- Sidechat: Community Guidelines; Users may report a post for removal by emailing support@sidechat.lol.
- Substack: Content Guidelines (“If you encounter content that may be in breach of these guidelines or have any questions about them, you can email us at tos@substackinc.com.”).
- TikTok: Community Guidelines; Report a Problem.
- Truth Social: Terms of Use § 7 (“Prohibited Activities”). While we were unable to find a reporting function on Truth Social, Section 32 of the Terms of Use document states as follows: “In order to resolve a complaint regarding the Service or to receive further information regarding use of the Service, please contact us at support@truthsocial.com. Users may report ‘hateful conduct,’ as defined by New York law, to legal@tmtgcorp.com.”
- WordPress: User Guidelines, Report a Site.
- X/Twitter: The X Rules, Report Violations.
- YouTube: Community Guidelines. To report content on YouTube, you can click the “Report” button underneath the video frame on each video’s webpage. To reveal the “Report” button, click the icon with three dots on it, just under the right-bottom corner of the video.
7. Remove your contact information from the Penn online directory.
If you are concerned that online harassers can direct harassing communications to you using information found in the Penn Directory, you may opt-out of sharing certain information.
The Directory offers two views of information:
- The Public View, available to anyone on the Internet
- The Penn View, available only to authorized users — primarily Penn students, faculty, and staff — who must log in using their PennKey and password
Many data fields are available in an individual’s Penn Directory profile. Some fields are pre-populated and can be edited or concealed; others appear blank and can be filled in voluntarily. Individuals are free to decide which information to display based on their personal privacy needs and the following requirements:
- Students are not required to display any data in the Penn Directory
- Faculty and staff have minimum listing requirements designed to balance personal privacy needs with the University’s operational needs:
- Public View: Name and affiliation
- Penn View: Name, School or organization, affiliation, title, a campus mailing address, a campus phone number, and a campus email address.
Faculty and staff who have a compelling privacy or security concern that warrants exclusion from the Directory may submit a request for consideration to the Office of Audit, Compliance, and Privacy. Send requests to privacy@upenn.edu.
You may read further about these choices here: https://www.isc.upenn.edu/about-penns-online-directory
To change your Privacy Settings in the Penn Directory, follow these steps:
- On the Penn Directory Page, click on My Profile in the upper right corner:
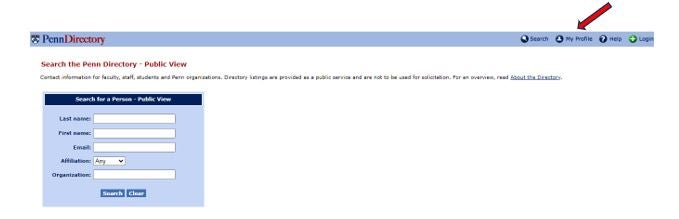
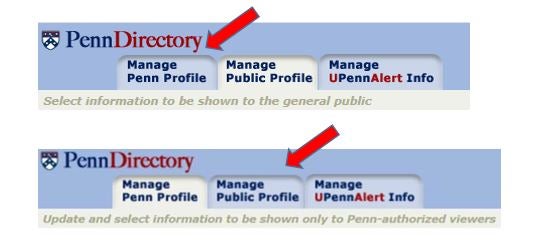
- Then select “Manage Penn Profile” or “Manage Public Profile”, depending upon which view you wish to edit. You will then be able to select the information by clicking on each button and indicating that you do not wish for certain information to appear to the public under “Manage Public Profile” or to individuals within Penn under “Manage Penn Profile”.
8. Preserve any relevant evidence
If you are subjected to online harassment, it can be helpful to maintain the evidence, particularly if the harassment escalates to a threat. You should:
- Save any emails, voicemails, or text messages you receive.
- Take screenshots or photos of comments on social media; because such comments can be deleted, screenshots are often useful to help document them.
While it may seem counterintuitive to keep message, posts or texts that are distressing or threatening, evidence of the online harassment may be needed down the line – particularly if you have made a report of online harassment to a social media platform, the Division of Public Safety, or another law enforcement entity.
